By: Michael Stokes, VP of Strategic Engagements
Executive Summary
In 2025, visibility, not obscurity, is the default in modern digital ecosystems; a reality that has made traditional cover harder to sustain, as reported by The Economist’s Technology Quarterly. Near-universal device and internet adoption reinforces that baseline. Across government and industry, the Office of the Director of National Intelligence (ODNI) formally recognizes that large pools of commercially available information (CAI) can be acquired and fused for analysis at scale under governance. At the city level, Human Rights Watch has documented how Moscow’s facial-recognition network enables real-time identification and retrospective tracing, demonstrating the operational reality of fused surveillance. Even seemingly harmless consumer exhaust can be revealing; WIRED showed how Strava’s public heat map illuminated bases and patrol routes, prompting a U.S. military review. To operate effectively in this environment, commanders should adopt Digital Signature Warfare (DSW) – a doctrine that aligns behavior and emissions before, during, and after operations to avoid investigative triggers, protect the operational act, and frustrate forensic reconstruction.
From Sensors to a Fused Data Ecosystem
Ubiquitous Technical Surveillance (UTS) is no longer a single-sensor problem. Data collection is a fused fabric of IoT devices, CCTV/biometrics, telecom metadata, connected-vehicle telemetry, and commercial datasets analyzed at machine scale. Within the U.S. government, the ODNI’s 2024 CAI framework codifies how purchasable, sensitive data can be accessed and processed under governance, reflecting the scope and persistence of modern data markets. At the population scale, the Pew Research Center reports that 98% of U.S. adults own a cellphone, and roughly nine in ten own a smartphone, making sustained “no-device/no-signal” behavior unusual in everyday life. China’s national initiatives illustrate what fused public-space surveillance looks like at scale: the Sharp Eyes and Skynet programs aim to extend camera coverage across cities and towns and fuse feeds for rapid identification and dispatch. Independent reporting by the UN human-rights office describes intrusive, tech-enabled surveillance as part of wider concerns in Xinjiang, underscoring how data from multiple vectors can be combined for control. Human Rights Watch has reverse-engineered the Xinjiang police “Integrated Joint Operations Platform,” showing how authorities flag “abnormal” behavior for investigation – an operational example of anomaly-driven tasking. An Associated Press investigation found that China’s predictive-policing and mass-surveillance build-out reinforces how multi-vector data can be combined and weaponized. Beyond China, city networks like Moscow’s leverage facial recognition to locate individuals quickly, underscoring that a single break in an established pattern of life can cue automated tasking. In practice, this means a force can be identified by how its patterns change, through procurement purchases, synchronized travel windows, and out-of-pattern routes, rather than by any single emitter or message.
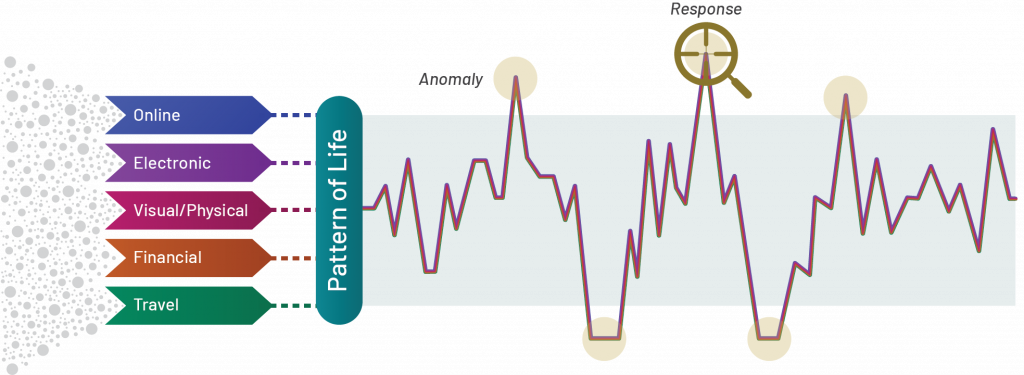
Figure 1. Ridgeline International’s Pattern of Life Anomaly Response (POLARTM) Model illustrates the conditions under which deviations from the patterns generated in commercial data can trigger adversary response.
For DoD, the U.S. Army describes UTS as pervasive collection across five vectors: online, financial, electronic, visual, and travel, enabling long-term reconstruction of events.
In Great Power Competition, that five-vector reality changes how we plan and fight. For Large Scale Combat Operations (LSCO), an adversary doesn’t need a single perfect intercept; they learn our logistics and movement baselines from ordinary digital exhaust, including fuel and toll records, charter and rail manifests, port and warehouse cameras, fleet telematics, payment cadence, and then alert on deviations that look like mobilization or staging. For supply chains, the same digital fabric can map routes, vendors, and surge timing from freight brokerage data, bills of lading, and facility telemetry. The counter is digital signature shaping at scale – build civilian-cohort noise before you need it, disperse your routes and vendors, time-shift loads, pre-age accounts and devices, and seed decoys so procurements, convoy patterns, and assembly areas read as routine rather than as an anomaly in the data.
For troop movements and Special Operations, Emission Control (EMCON) and “no phone” are necessary but no longer sufficient. Movement is discovered by correlation, not just by communications. The Pentagon Pizza Index is an example of an online tool used to start the investigation. From there, adversaries track data from vehicle telematics, and cell phones around known SOF bases and various public cameras can reveal fleet movement even when radios are quiet.
Why Digital Discipline is Not Enough
Leaving the phone behind used to feel sufficient. Today, it is only the baseline. Re-identification science shows that a few mobility points or attributes can uniquely identify most individuals in large datasets. Platforms in China demonstrate how a single break in routine can cue automated action. The Xinjiang police platform flags “abnormal” device use, movement, or social ties for follow-up. A Justice Department Inspector General audit summarized by Lawfare describes how the Sinaloa cartel mixed phone data with Mexico City cameras to identify and intimidate U.S. contacts – an example of fused replay outside a state surveillance system. Complementary reporting by Homeland Security Today details the “Sinaloa hack of an FBI phone,” highlighting operational risks at the edge of fused technical surveillance.
The Salt Typhoon cyberattack compromised the core networks of major telecom and internet service providers, including AT&T, Verizon, and Lumen Technologies. By gaining a foothold in the very systems that route communications, they were positioned to intercept, steal, and surveil data, as well as monitor a vast amount of traffic. This attack proves that even US infrastructure is not impervious to attack and compromise by near peer adversaries.
Third-party exhaust surrounds every mission. Data-broker ecosystems and ad-tech telemetry continue to circulate sensitive location data despite nominal opt-outs, as evidenced by the FTC’s case against Kochava and an investigation by WIRED, The Markup, and CalMatters that found dozens of brokers hiding opt-out pages from search.
Complete withdrawal is impractical. Communications, finance, travel, and logistics rely on personal and location data, and both governments and platforms collect this information extensively.
Because commercial data is collected continuously and stored indefinitely, there is a permanent data record of any connection, travel, purchase, or activity. Understanding the full impact of UTS on operations in this fused data ecosystem context requires conceptualizing the operational act in three parts: the act itself; the period to the “left of bang” where research, planning, and preparation take place; and the period to the “right of bang” where adversaries will investigate and act based on forensic clues left at the “X” – the operational site.
When adversaries leverage UTS to create baselines for our data output and flag breaks in our patterns of life, operational success depends less on last-minute evasions or the use of burner phones, than on shaping what the system sees over time. To mitigate these threats, we must avoid investigative triggers before the act, prevent observation during the act, and mitigate forensic reconstruction or attribution once the act has taken place.
New Doctrine: Digital Signature Warfare
Digital Signature Warfare turns your digital signature from a liability into an asset across the full mission timeline, aligning behavior and emissions before, during, and after operations.
DSW executes through four actions:
- SEE: using a Digital Mirror to assess discoverability and cohort fit
- SHAPE: choosing plausible narratives and measurable shifts
- CONTROL: enforcing emissions and behavior that fit those narratives
- DECEIVE: misleading adversary models with cover-consistent misdirection
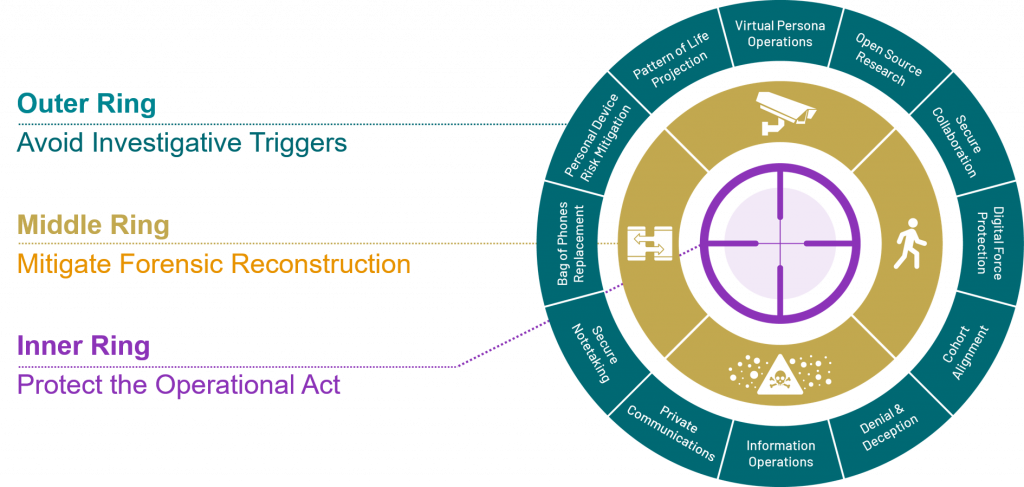
Figure 2: Protecting operations requires confronting UTS threats before, during, and after the operational act by offensively and defensively managing digital signatures.
These actions, when overlaid on the three-part timeline of an operational act (left of bang, the operational act, right of bang), create a framework for keeping our observable data within pattern to avoid investigative triggers, protect the “X”, and mitigate forensic reconstruction.
The Three Rings of UTS Mitigation
Outer Ring | Before | Avoid Investigative Triggers: The best outcome is that the adversary never looks. Keep the operator indistinguishable from the cover cohort by maintaining continuity in daily rhythms, venues, and payment patterns, and by avoiding synchronized “dark” windows that deviate from baseline. In a smart city where cameras and data registries are fused, repeated day-long handset silence can act as a soft tag that elevates tasking priority; Chinese deployments show how fused systems can operationalize such cues at scale. Even though China has signaled that guardrails are needed – its cyberspace regulator issued rules saying facial recognition should not be forced on individuals and must have visible signage – the structural capability remains extensive.
Inner Ring | During | Protect the Operational Act: Do not expose the act. Leave electronics behind, and choose movement that minimizes person/sensor coupling by flowing within cover-cohort pulses and avoiding camera-dense chokepoints.
Middle Ring | After | Mitigate Forensic Reconstruction: Assume the adversary detected that something happened. Deny a clean chain across the five UTS vectors so replay yields ambiguity, not attribution. Police platforms in China demonstrate the replay risk: multi-vector logs – devices, checkpoints, cameras, registries – can be rewound to stitch together people, places, and timelines unless the data yields ambiguity.
Because simply leaving phones behind, using burner phones, or practicing good digital discipline are not enough, a new and comprehensive approach is required to maintain our competitive advantage in the UTS environment.
A New Approach & Implementation
Capabilities without Brands
The point of capability isn’t the gear on the table; it’s the effect you can deliver in a UTS fight. The disciplines listed below serve as functional building blocks. Used together, they create the outcomes the mission needs over time: avoiding investigative triggers (Outer Ring), protecting the operational act (Inner Ring), and frustrating forensic reconstruction (Middle Ring). Integrated and exercised as a system-of-systems, they let commanders see, shape, control, and deceive what the environment and adversary learn about their force.
Digital Signature Management (Digital Mirror)
A mission-controlled view of the same classes of signals an adversary would use – ad-tech location, mobility traces, building/venue telemetry, and open/closed sources – lets leaders visualize discoverability, run what-if tests, and quantify ambiguity under replay. As a practical benchmark, model Digital Mirrors on the kinds of anomaly flags documented in Xinjiang, and test whether small changes in timing, routes, and device posture suppress or elevate alerts.
Managed Attribution & Device Virtualization
Cover-consistent identities and devices with controllable sensors, plausible account age, and local usage cadence help preserve continuity when the real handset stays behind. Diversified points-of-presence – residential, commercial, cloud, LTE edges – reduce tie-back and prevent sterile-phone tells.
Secure Mobility Enclaves & Enterprise Mobility Management
Layered mobility such as mobile device managers (MDM), enterprise mobility managers (EMM), dedicated Access Point Names (APN), and encryption profiles compartment sensitive work into mission enclaves and enforces policy without advertising unusual behavior to the outside world, supporting Outer Ring discipline and Middle Ring isolation.
Secure Collaboration & Data Hygiene
Zero-trust collaboration in dedicated workspaces reduces third-party leakage during planning. Ongoing data-broker hygiene minimizes coincidental linkages that can light up an operator or family member under replay. A WIRED investigation found many brokers hiding opt-out pages from search, which explains why deletion and suppression often require persistent effort.
Training & Assessment Cadence
Progressive education and exercises – hands-on device configuration, synthetic smart-city ranges, and red-cell events with commercial data – convert doctrine into judgment under stress and feed measured outcomes back into SOPs. Where possible, incorporate PRC-style fused scenarios such as camera saturation, registry checks, and watchlist hits so teams practice staying cohort-consistent under the same pressures they will face in contested environments.
Policy & Culture
Addressing this evolving threat requires more that an adjustment to tactics. Transformational change to the mindset, culture, and policy that governs these actions is necessary to effectively meet the challenges posed by UTS.
Treat digital-signature management as mission-critical, not an IT afterthought, and tie signature metrics to readiness reporting. Assume regional diffusion of Chinese surveillance AI, which academic research shows China exports at scale, especially to autocracies and weak democracies, shaping the operating environment beyond its borders. As Lawfare argues, broader U.S. data protections would directly reduce commercial-surveillance risk and lower the mitigation burden for operators. Track three measures of effectiveness: trigger rate (how often anomalies are generated), correlation depth (how many vectors align), and reconstruction error (ambiguity after replay), and use them to drive training and resourcing decisions.
Implementation
This transition should be implemented in stages to achieve a comprehensive understanding and data-informed approach to UTS mitigation.
See Yourself: Stand up a Digital Mirror that emulates local anomaly detection (device clustering, venue cadence, cohort fit) and measures unit discoverability against city baselines. Treat this as a comprehensive UTS survey tied to commander decisions.
Shape & Control: Publish Outer Ring standards for cohort alignment, device posture, and normalized absence so occasional “no-phone” days are already part of the baseline. Pre-provision persona devices with plausible account age, app constellation, and usage cadence.
Test & Iterate: Conduct right-of-bang drills in which a red team attempts forensic reconstruction using public and commercial data. Use realistic red cells with access to commercial sensors, broker data, and building telemetry to validate DSW under smart-city conditions. Update TTPs and SOPs based on measurable ambiguity: trigger rate, correlation depth, and reconstruction error.
Consider Coalition Impact: Train, audit, and equip partners to the same Digital Signature Warfare standards. Cohesive signature doctrine reduces third-party bleed in mixed formations.
Conclusion
Visibility is normal. Obscurity is exceptional. Forces that shape their signature before, during, and after operations keep time, choice, and surprise – advantages that matter in any theater. The threat landscape is shifting faster than ever before: smart-city cameras, brokered data, and AI correlation turn everyday exhaust into targeting information, making visibility the baseline and anomalies the trigger. Digital Signature Warfare answers that reality by moving from episodic “comms discipline” to continuous, commander-led signature management across people, devices, movements, payments, and procurement. Units that institutionalize DSW through application of the Three Rings framework and measurable standards lower their trigger rate, raise forensic reconstruction error, and cut the cost of secrecy across LSCO mobilizations, sustainment flows, troop movements, and SOF missions. The objective is not to vanish, but to blend – to look like the cohort the mission demands before, during, and after the act. Forces that do this regain initiative, extend survivability, and impose uncertainty on adversary targeting and decision cycles. That is how the United States and its allies convert UTS from an asymmetric disadvantage into an operational edge, improving mission safety today and preserving strategic advantage in great-power competition.
Disclaimer: All statements of fact, opinion, or analysis expressed are those of the author and do not reflect the official positions or view of the US Government. Nothing in the contents should be construed as asserting or implying US Government authentication of information or endorsement of the author’s views.
